


Pentagon wants to make AI acceleration initiative a long-term fixture
The Pentagon is crafting a plan to make its AI and Data Acceleration initiative a more permanent fixture within combatant commands.

Opinion
How the military is preparing for AI at the edge
DoD must adopt solutions with significant computing power at the edge, find ways to reduce the size of AI/ML models and mitigate new security threats.

Safran in talks to buy French AI startup Preligens for €220 million
The Paris-based company's algorithms are used to analyze satellite data for the French and U.S. militaries.

Opinion
The best way to counter bad artificial intelligence is using good AI
iI’s critical that policymakers avoid focusing too narrowly on catastrophic risk and inadvertently hamstring the creation of positive AI tools,.

US Army to launch AI pilot project for acquisition workforce
The pilot project is part of a broader effort within the Army to identify both the pitfalls and the opportunities that come with widely adopting AI tools.

France preps Europe’s fastest classified supercomputer for defense AI
French defense leaders plan a leading role in mastering AI, considered to be a key differentiating factor among tomorrow's armed forces.

MBDA unveils AI-based Ground Warden tool for finding hidden targets
MBDA makes a similarly named platform, the Sky Warden, which is a counter-drone system designed to control a large range of sensors and effectors.

Opinion
How to harness AI and Zero Trust segmentation to boost cyber defenses
More than half of leaders who have implemented AI say that it's helped accelerate incident response times, highlighting the technology's potential.

Air Force, Space Force unveil tool for AI experimentation
The services want to use the tool to better understand how AI could improve access to information and to gauge whether there’s demand within the force.

DARPA sees automated tools helping streamline software certification
There are tools that can look at file metadata, which contains proof that the software is secure, and automatically verify its safety.

AI regulators fear getting drowned out by hype of wars
Advocates for limiting artificial intelligence in combat say the global security environment isn't conducive to their cause, but interest remains.

Opinion
Leveraging AI, digital twins, AR/VR for military aircraft maintenance
A lack of existing digital models severely hampers operational efficiency, mission planning and aircraft readiness.

Palantir wins contract to expand access to Project Maven AI tools
The five-year contract will allow the Defense Department to expand the Maven Smart System's use to thousands of users at five combatant commands.
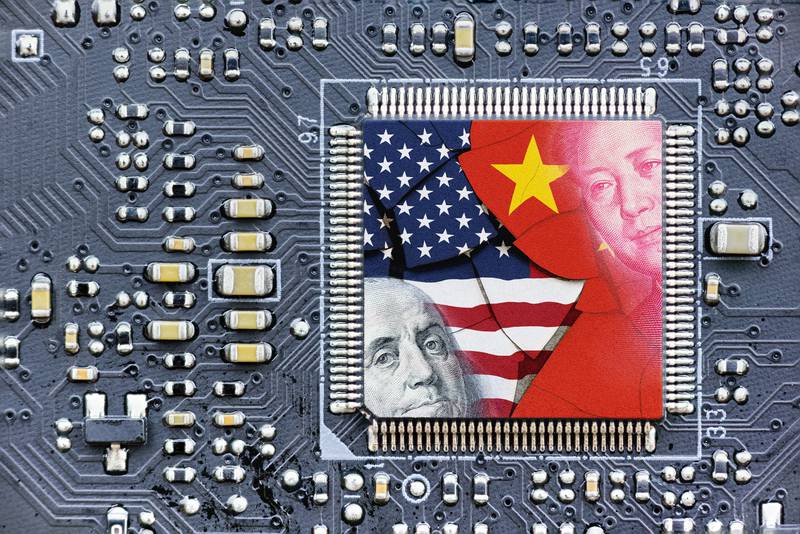
Opinion
All that’s left: A self-defeating semiconductor export tactic for China
If we do not get our semiconductor export control strategy right, not much else matters when it comes to the technology arms race with China.

Opinion
How real-time search analytics and AI can help the DOD break down data
Tearing down data silos and achieving data interoperability is a complex and challenging task.

France turns to AI for signals analysis in underwater acoustics war
French naval intelligence analysts want to hear a wrench falling in a hold in a faraway vessel, or its pumps starting up.

US aims to outpace China with AI on fighter jets, navigation and more
The United States is competing to stay ahead of China on AI and its use in weapon systems.
